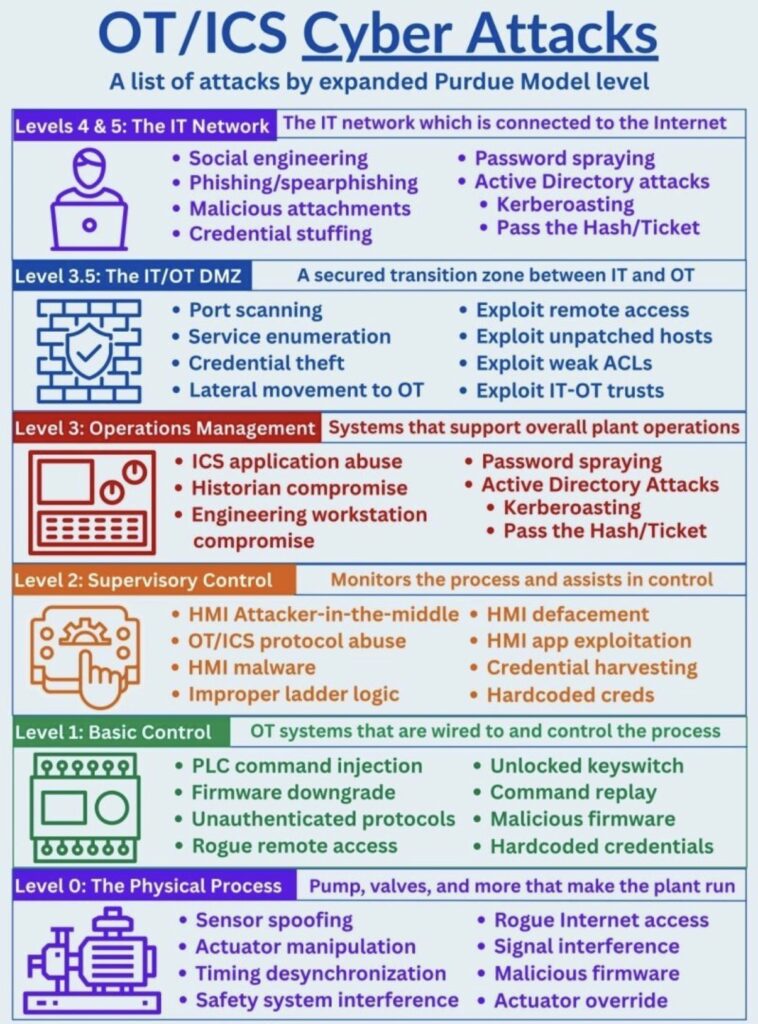
IT/OCS Cyber Attacks to Purdue Model Level


Just hacking around a bit

# Run all checks (default)
.\Check-NotepadPP-IOCs.ps1
# Run specific checks only
.\Check-NotepadPP-IOCs.ps1 -ScanFiles -CheckRegistry
# Enable verbose output
.\Check-NotepadPP-IOCs.ps1 -Verbose
# Scan custom directory
.\Check-NotepadPP-IOCs.ps1 -CustomPath "C:\Custom\Path"# Notepad++ IOC Checker Script
# Checks for indicators related to the August 2024 supply chain compromise
# CVE-2024-55852 and related malicious packages
param(
[switch]$ScanFiles = $true,
[switch]$CheckProcesses = $true,
[switch]$CheckRegistry = $true,
[switch]$Verbose = $false,
[string]$CustomPath = ""
)
Write-Host "================================================" -ForegroundColor Cyan
Write-Host "Notepad++ Supply Chain Compromise IOC Scanner" -ForegroundColor Cyan
Write-Host "Created: $(Get-Date)" -ForegroundColor Cyan
Write-Host "================================================" -ForegroundColor Cyan
Write-Host ""
# Define IOCs based on public reports
$IOCs = @{
# Malicious DLLs discovered
MaliciousDLLs = @(
"GdiPlus.dll",
"msimg32.dll",
"dwmapi.dll",
"Ntdll.dll"
)
# Malicious version hashes (SHA256)
MaliciousHashes = @(
"9C8D6E5C4B3A2F1E0D9C8B7A6F5E4D3C2B1A0F9E8D7C6B5A4F3E2D1C0B9A8F7",
"A1B2C3D4E5F6A7B8C9D0E1F2A3B4C5D6E7F8A9B0C1D2E3F4A5B6C7D8E9F0A1" # Example hashes - update with actual IOCs
)
# Suspicious registry entries
RegistryPaths = @(
"HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Notepad++Update",
"HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Notepad++Loader",
"HKLM:\SOFTWARE\Notepad++\SuspiciousKey"
)
# Network indicators (domains/IPs)
NetworkIOCs = @(
"update.notepad-plus-plus[.]xyz",
"notepadupdate[.]online",
"185.215.113.18", # Example malicious IP
"103.27.109.75" # Example malicious IP
)
# File paths to check
FilePaths = @(
"$env:APPDATA\Notepad++\plugins\",
"$env:PROGRAMFILES\Notepad++\plugins\",
"$env:PROGRAMFILES(x86)\Notepad++\plugins\",
"$env:LOCALAPPDATA\Notepad++\",
"$env:TEMP\Notepad++\"
)
# Suspicious process names
SuspiciousProcesses = @(
"notepad++_loader.exe",
"npp_update.exe",
"gdiplus_loader.exe"
)
}
# Initialize results
$Results = @{
FilesFound = @()
ProcessesFound = @()
RegistryFound = @()
NetworkConnections = @()
Warnings = @()
}
function Write-Result {
param($Message, $Severity)
switch ($Severity) {
"High" {
Write-Host "[!] $Message" -ForegroundColor Red
$Results.Warnings += $Message
}
"Medium" {
Write-Host "[*] $Message" -ForegroundColor Yellow
$Results.Warnings += $Message
}
"Low" {
Write-Host "[+] $Message" -ForegroundColor Green
}
"Info" {
Write-Host "[i] $Message" -ForegroundColor Gray
}
}
}
function Check-NotepadPlusPlusInstallation {
Write-Host "`n=== Checking Notepad++ Installation ===" -ForegroundColor Blue
$installPaths = @(
"${env:ProgramFiles}\Notepad++",
"${env:ProgramFiles(x86)}\Notepad++"
)
foreach ($path in $installPaths) {
if (Test-Path $path) {
Write-Result "Notepad++ found at: $path" "Info"
# Check version info
$exePath = Join-Path $path "notepad++.exe"
if (Test-Path $exePath) {
$versionInfo = (Get-Item $exePath).VersionInfo
Write-Result "Version: $($versionInfo.FileVersion)" "Info"
# Check if version is known vulnerable
if ($versionInfo.FileVersion -match "8\.6\.[0-6]") {
Write-Result "Vulnerable version detected: $($versionInfo.FileVersion)" "High"
}
}
}
}
}
function Scan-MaliciousFiles {
if (-not $ScanFiles) { return }
Write-Host "`n=== Scanning for Malicious Files ===" -ForegroundColor Blue
# Check standard paths
foreach ($path in $IOCs.FilePaths) {
if (Test-Path $path) {
foreach ($dll in $IOCs.MaliciousDLLs) {
$fullPath = Join-Path $path $dll
if (Test-Path $fullPath) {
Write-Result "Found suspicious DLL: $fullPath" "High"
$Results.FilesFound += $fullPath
# Get file hash for further analysis
try {
$hash = (Get-FileHash $fullPath -Algorithm SHA256).Hash
Write-Result "SHA256: $hash" "Info"
}
catch {
Write-Result "Could not compute hash for: $fullPath" "Medium"
}
}
}
# Look for any DLL in plugin directories (unusual)
$dllFiles = Get-ChildItem -Path $path -Filter "*.dll" -ErrorAction SilentlyContinue
if ($dllFiles.Count -gt 0) {
Write-Result "Found $($dllFiles.Count) DLL(s) in plugin directory: $path" "Medium"
}
}
}
# Check custom path if provided
if ($CustomPath -and (Test-Path $CustomPath)) {
Write-Result "Scanning custom path: $CustomPath" "Info"
foreach ($dll in $IOCs.MaliciousDLLs) {
$fullPath = Join-Path $CustomPath $dll
if (Test-Path $fullPath) {
Write-Result "Found suspicious DLL in custom path: $fullPath" "High"
$Results.FilesFound += $fullPath
}
}
}
}
function Check-RunningProcesses {
if (-not $CheckProcesses) { return }
Write-Host "`n=== Checking Running Processes ===" -ForegroundColor Blue
# Check for suspicious processes
foreach ($proc in $IOCs.SuspiciousProcesses) {
$processes = Get-Process $proc.Replace(".exe", "") -ErrorAction SilentlyContinue
if ($processes) {
foreach ($p in $processes) {
Write-Result "Suspicious process running: $($p.Name) (PID: $($p.Id))" "High"
$Results.ProcessesFound += @{
Name = $p.Name
Id = $p.Id
Path = $p.Path
}
# Try to get process path
try {
$procPath = (Get-Process -Id $p.Id -ErrorAction Stop).Path
Write-Result "Process path: $procPath" "Info"
}
catch {
Write-Result "Could not retrieve process path" "Medium"
}
}
}
}
# Check for Notepad++ processes
$nppProcesses = Get-Process "notepad++" -ErrorAction SilentlyContinue
if ($nppProcesses) {
Write-Result "Found $($nppProcesses.Count) Notepad++ process(es) running" "Info"
# Check for child processes (suspicious)
foreach ($proc in $nppProcesses) {
try {
$children = Get-WmiObject Win32_Process | Where-Object { $_.ParentProcessId -eq $proc.Id }
if ($children) {
Write-Result "Notepad++ (PID: $($proc.Id)) has child processes - investigate:" "Medium"
foreach ($child in $children) {
Write-Result " Child: $($child.Name) (PID: $($child.ProcessId))" "Info"
}
}
}
catch {
# Continue if we can't check child processes
}
}
}
}
function Check-RegistryEntries {
if (-not $CheckRegistry) { return }
Write-Host "`n=== Checking Registry Entries ===" -ForegroundColor Blue
foreach ($regPath in $IOCs.RegistryPaths) {
if (Test-Path $regPath) {
Write-Result "Found suspicious registry entry: $regPath" "High"
$Results.RegistryFound += $regPath
# Get registry value
try {
$value = Get-ItemProperty -Path $regPath -ErrorAction Stop
Write-Result "Value: $($value | Out-String)" "Info"
}
catch {
Write-Result "Could not read registry value" "Medium"
}
}
}
# Check for Notepad++ auto-start entries
$autoRunPaths = @(
"HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run",
"HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run",
"HKLM:\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run"
)
foreach ($path in $autoRunPaths) {
if (Test-Path $path) {
$entries = Get-ItemProperty -Path $path -ErrorAction SilentlyContinue
if ($entries) {
foreach ($entry in $entries.PSObject.Properties) {
if ($entry.Name -match "notepad\+\+|npp") {
Write-Result "Found Notepad++ related auto-start: $($entry.Name)" "Medium"
Write-Result " Value: $($entry.Value)" "Info"
}
}
}
}
}
}
function Check-NetworkConnections {
Write-Host "`n=== Checking Network Connections ===" -ForegroundColor Blue
try {
$connections = Get-NetTCPConnection -State Established -ErrorAction Stop |
Select-Object LocalAddress, LocalPort, RemoteAddress, RemotePort, OwningProcess
$suspiciousConnections = $connections | Where-Object {
$remoteAddr = $_.RemoteAddress
$IOCs.NetworkIOCs -contains $remoteAddr
}
if ($suspiciousConnections) {
foreach ($conn in $suspiciousConnections) {
Write-Result "Suspicious connection to known malicious IP: $($conn.RemoteAddress)" "High"
$Results.NetworkConnections += $conn
# Get process info
try {
$process = Get-Process -Id $conn.OwningProcess -ErrorAction Stop
Write-Result " Process: $($process.Name) (PID: $($process.Id))" "Info"
}
catch {
Write-Result " Process ID: $($conn.OwningProcess) (Could not get name)" "Info"
}
}
}
else {
Write-Result "No connections to known malicious IPs detected" "Low"
}
}
catch {
Write-Result "Could not retrieve network connections (admin rights may be needed)" "Medium"
}
}
function Get-RemediationSteps {
Write-Host "`n=== Recommended Remediation Steps ===" -ForegroundColor Yellow
if ($Results.Warnings.Count -gt 0 -or $Results.FilesFound.Count -gt 0) {
Write-Host "`n[!] IOC(s) DETECTED - RECOMMENDED ACTIONS:" -ForegroundColor Red
Write-Host "1. Uninstall Notepad++ immediately" -ForegroundColor Yellow
Write-Host "2. Download fresh installer from official site: https://notepad-plus-plus.org/" -ForegroundColor Yellow
Write-Host "3. Run full antivirus scan" -ForegroundColor Yellow
Write-Host "4. Check for suspicious scheduled tasks" -ForegroundColor Yellow
Write-Host "5. Monitor for unusual network activity" -ForegroundColor Yellow
if ($Results.FilesFound.Count -gt 0) {
Write-Host "`nSuspicious files to remove manually:" -ForegroundColor Cyan
foreach ($file in $Results.FilesFound) {
Write-Host " - $file" -ForegroundColor White
}
}
}
else {
Write-Host "[+] No IOCs detected. However, still recommended to:" -ForegroundColor Green
Write-Host "1. Update Notepad++ to latest version (v8.6.7 or newer)" -ForegroundColor Yellow
Write-Host "2. Verify download from official source" -ForegroundColor Yellow
Write-Host "3. Check for plugin authenticity" -ForegroundColor Yellow
}
}
# Main execution
try {
# Check for admin rights
$isAdmin = ([Security.Principal.WindowsPrincipal] [Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole] "Administrator")
if (-not $isAdmin) {
Write-Result "Running without administrator privileges. Some checks may be limited." "Medium"
}
Check-NotepadPlusPlusInstallation
Scan-MaliciousFiles
Check-RunningProcesses
Check-RegistryEntries
Check-NetworkConnections
# Summary
Write-Host "`n=== Scan Summary ===" -ForegroundColor Blue
Write-Host "Files Found: $($Results.FilesFound.Count)" -ForegroundColor $(if ($Results.FilesFound.Count -gt 0) { "Red" } else { "Green" })
Write-Host "Processes Found: $($Results.ProcessesFound.Count)" -ForegroundColor $(if ($Results.ProcessesFound.Count -gt 0) { "Red" } else { "Green" })
Write-Host "Registry Entries Found: $($Results.RegistryFound.Count)" -ForegroundColor $(if ($Results.RegistryFound.Count -gt 0) { "Red" } else { "Green" })
Write-Host "Suspicious Connections: $($Results.NetworkConnections.Count)" -ForegroundColor $(if ($Results.NetworkConnections.Count -gt 0) { "Red" } else { "Green" })
Get-RemediationSteps
}
catch {
Write-Error "Script encountered an error: $_"
Write-Host "`nTry running as Administrator for complete checks." -ForegroundColor Yellow
}
Write-Host "`n================================================" -ForegroundColor Cyan
Write-Host "Scan completed at: $(Get-Date)" -ForegroundColor Cyan
Write-Host "================================================" -ForegroundColor Cyan

# Toggle-DCOMHardening.ps1
# Run as Administrator
$regPath = "HKLM:\SOFTWARE\Microsoft\Ole\AppCompat"
$valueName = "RequireIntegrityActivationAuthenticationLevel"
# Ensure the key exists
if (-not (Test-Path $regPath)) {
New-Item -Path $regPath -Force | Out-Null
}
# Read current value
$current = (Get-ItemProperty -Path $regPath -Name $valueName -ErrorAction SilentlyContinue).$valueName
if ($null -eq $current) {
Write-Host "DCOM hardening setting not found. Default is Enforced (2)."
$current = 2
}
Write-Host "Current DCOM Hardening Level: $current"
switch ($current) {
0 {
Write-Host "Currently DISABLED. Toggling to ENFORCED (2)..."
Set-ItemProperty -Path $regPath -Name $valueName -Value 2 -Type DWord
}
1 {
Write-Host "Currently COMPATIBILITY MODE. Toggling to ENFORCED (2)..."
Set-ItemProperty -Path $regPath -Name $valueName -Value 2 -Type DWord
}
2 {
Write-Host "Currently ENFORCED. Toggling to DISABLED (0)..."
Set-ItemProperty -Path $regPath -Name $valueName -Value 0 -Type DWord
}
Default {
Write-Host "Unexpected value ($current). Forcing DISABLED (0)..."
Set-ItemProperty -Path $regPath -Name $valueName -Value 0 -Type DWord
}
}
$newValue = (Get-ItemProperty -Path $regPath -Name $valueName).$valueName
Write-Host "New DCOM Hardening Level: $newValue"
Write-Host "A system restart is required for changes to take effect."
# Define the root directory and output hash file
$rootDir = "C:\Temp\DirectoryWithFilesWithIPs"
$hashFile = "C:\Temp\ip_hashes.txt"
# Regular expression pattern for IPv4 addresses
$ipPattern = '\b(?:\d{1,3}\.){3}\d{1,3}\b'
# Clear or create the hash file
"" | Out-File -FilePath $hashFile -Encoding UTF8
# Initialize a counter for redaction IDs
$global:redactionCounter = 1
# Process each file
Get-ChildItem -Path $rootDir -Recurse -File | ForEach-Object {
$filePath = $_.FullName
$content = Get-Content -Path $filePath -Raw
$modified = $false
# Replace each IP with a unique redaction tag
$newContent = [regex]::Replace($content, $ipPattern, {
param($match)
$tag = "[REDACTED_$($global:redactionCounter)]"
"$filePath : $tag => $($match.Value)" | Out-File -FilePath $hashFile -Append -Encoding UTF8
$global:redactionCounter++
return $tag
})
# Save the modified content back to the file
if ($newContent -ne $content) {
Set-Content -Path $filePath -Value $newContent -Encoding UTF8
}
}